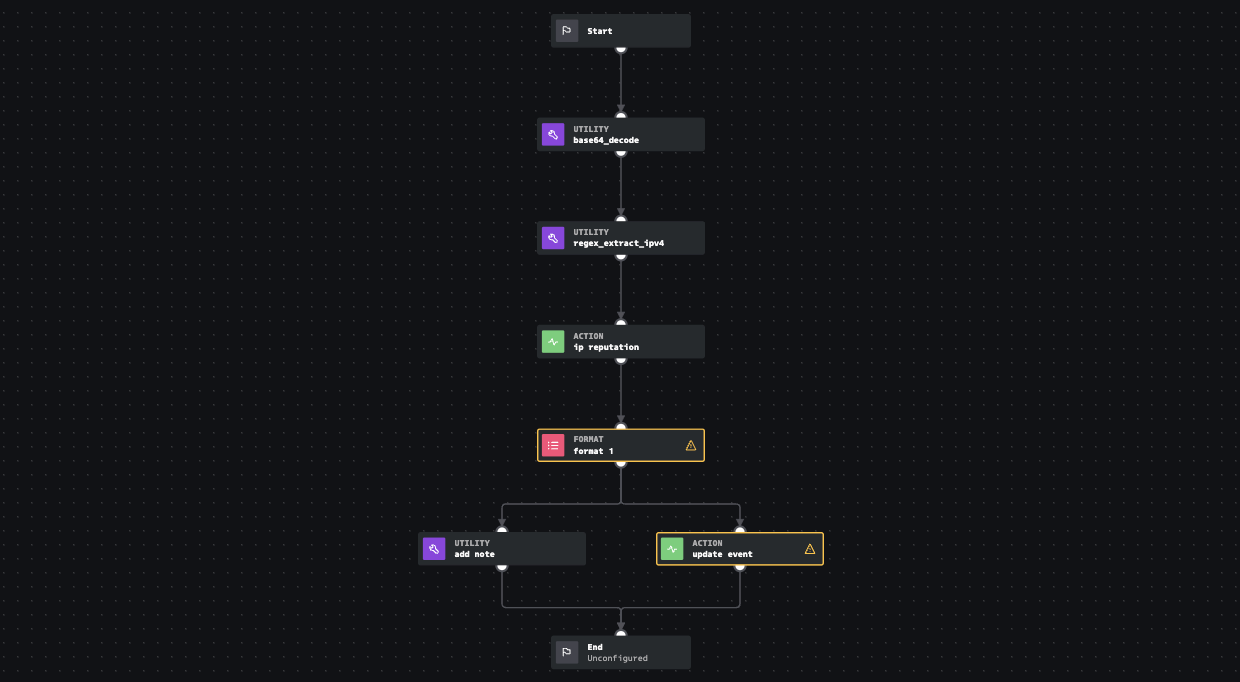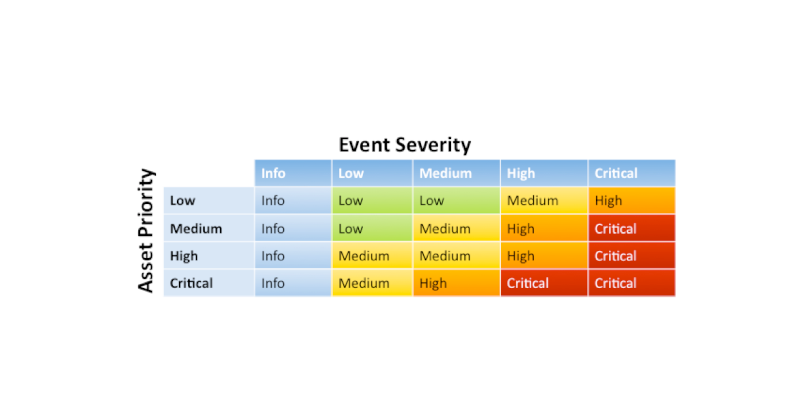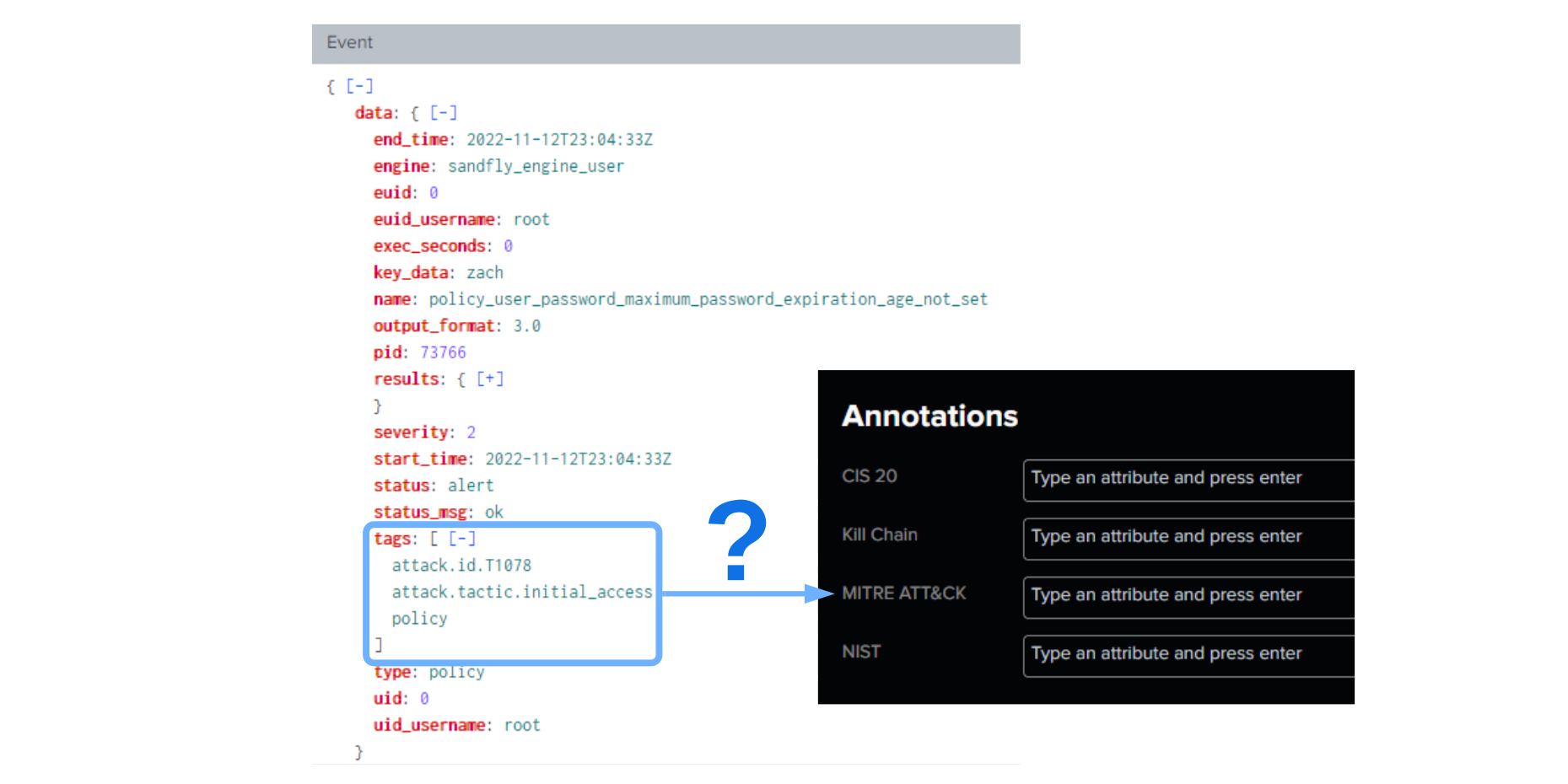
Advancing Cyber Defense: How PRE Security Predicts Threats Before They Strike
Traditional reactive models are no longer sufficient in today’s cyber threat landscape. PRE Security was founded on a bold premise: what if organizations could predict cyber events before they ca...